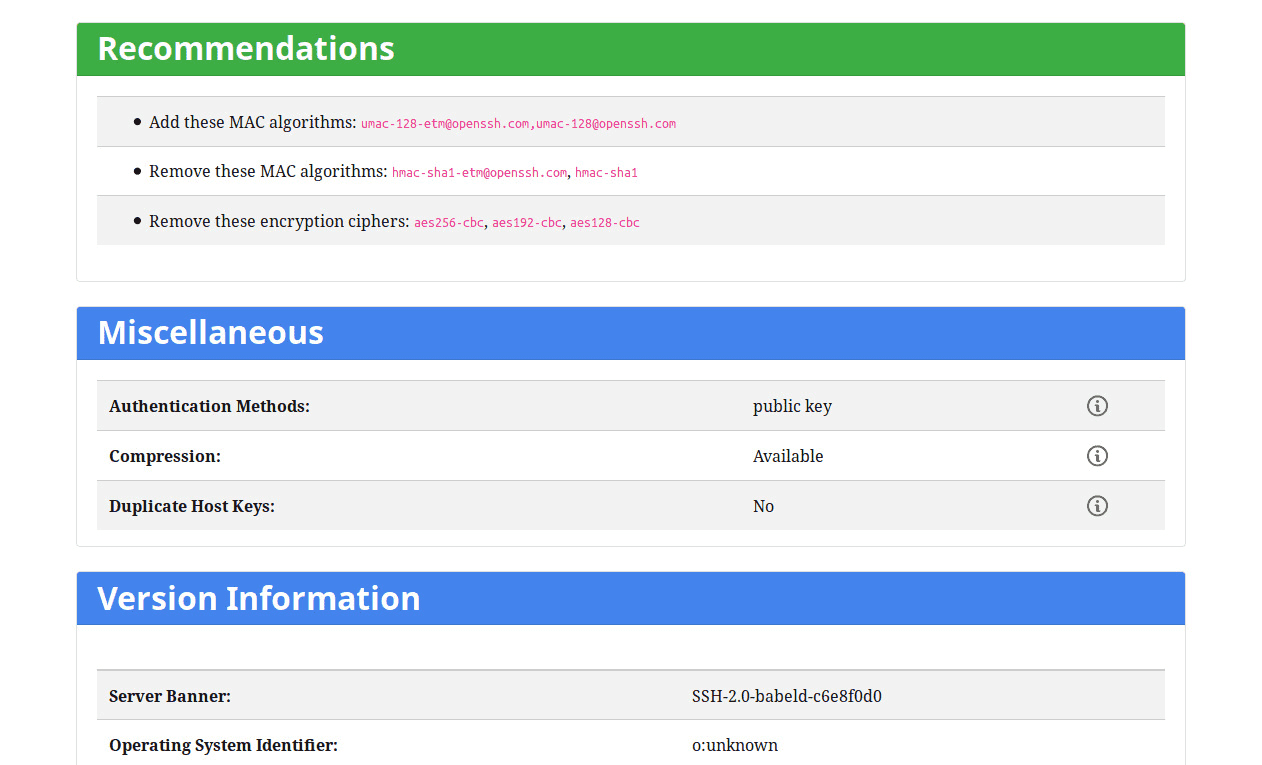
ssh-hmacs hmac-sha2-512 hmac-sha2-384 hmac-sha2-256 hmac-sha1 hmac-md5 hmac-ripemd160 ssh-compression zlib none WSFTP Professional 12.6 As of version 12.6, the 'diffie-hellman-group-exchange-sha256' ssh-kex and sha2 ssh-hmacs algorithms have been added as seen below: ssh-kex diffie-hellman-group-exchange-sha256 diffie-hellman-group.
Previously the fingerprint was given as a hexed md5 hash. Starting with OpenSSH 6.8 the fingerprint is now displayed as base64 SHA256 (by default). You can't compare these directly. They also added a new configuration option FingerprintHash. SSH (Secure Shell) is a network protocol that enables secure remote connections between two systems. System admins use SSH utilities to manage machines, copy, or move files between systems. Because SSH transmits data over encrypted channels, security is at a high level. This article will guide you through the most popular SSH commands.
SHA-256 produces a 256-bit (32-byte) hash value.
# What is SHA-256?
The SHA (Secure Hash Algorithm) is one of a number of cryptographic hash functions. A cryptographic hash is like a signature for a data set. If you would like to compare two sets of raw data (source of the file, text or similar) it is always better to hash it and compare SHA256 values. It is like the fingerprints of the data. Even if only one symbol is changed the algorithm will produce different hash value. SHA256 algorithm generates an almost-unique, fixed size 256-bit (32-byte) hash. Hash is so called a one way function. This makes it suitable for checking integrity of your data, challenge hash authentication, anti-tamper, digital signatures, blockchain.
With the newest hardware (CPU and GPU) improvements it is become possible to decrypt SHA256 algorithm back. So it is no longer recommended to use it for password protection or other similar use cases. Some years ago you would protect your passwords from hackers by storing SHA256 encrypted password in the your data base. This is no longer a case.
SHA256 algorithm can be still used for making sure you acquired the same data as the original one. For example if you download something you can easily check if data has not changed due to network errors or malware injection. You can compare hashes of your file and original one which is usually provided in the website you are getting data or the file from.
SHA-256 is one of the successor hash functions to SHA-1,and is one of the strongest hash functions available.
Using this online tool you can easily generate SHA256 hashes.
Home |FAQ |Feedback |Licence |Updates |Mirrors |Keys |Links |Team
Download:Stable ·Pre-release ·Snapshot |Docs |Changes |Wishlist
class: wish: This is a request for an enhancement.
difficulty
Sha256 Ssh-keygen
: tricky: Needs many tuits.priority: medium: This should be fixed one day.
fixed-in: 2021-03-14 66265d30f513c0496d9f3f882cf61b49f4bfff40 (0.75)
PuTTY currently only supports one format for displaying SSH public keyfingerprints (used whenverifying host keys);this is the traditional set of hex octets calculated with the MD5 hashfunction specified by section 4 ofRFC4716 (for instancessh-rsa 1024 7b:e5:6f:a7:f4:f9:81:62:5c:e3:1f:bf:8b:57:6c:5a).
New versions of OpenSSH (from6.8) defaultto displaying a different, base64-format fingerprint for certain keys, withcurrent versions calculated using the SHA-256 hash (for instanceSHA256:mVPwvezndPv/ARoIadVY98vAC0g+P/5633yTC4d/wXE).
Since modern OpenSSH takes some persuasion to display fingerprints inthe old format, and we should be moving away from the weak MD5 hashanyway, PuTTY should support displaying fingerprints in this newformat, as well as continuing to display the old format for backwardcompatibility.
Ssh Show Sha256 Fingerprint
We'd have to work out a UI for this. The obvious option is to displaythe fingerprint in all known formats in the host-key verificationdialog; this will make the dialog even more intimidating, and couldget unwieldy if we ever have more than two.A more complicated option would be to have a dropdown or buttons orsomething on the host-key dialog to let the user choose among theavailable formats; this probably implies a global setting to set thedefault (and PuTTY isn't currently very good at global settings).
(Should you need to get an MD5 fingerprint out of modern OpenSSH inthe meantime, you need to run a command likeon the relevant server.)
Some places where key fingerprints are currently used, so that extraUI complexity would need to be designed and implemented:
- The GUI dialog box (both Windows and GTK) asking for a host keyconfirmation. Obvious possibilities include a dropdown list offingerprint types, or simply listing all the known ones in a hugeinfo-dump. [We ended up listing SHA-256 by default, and puttingother formats behind a 'More info...' button.]
- The corresponding console message, which can't provide a dropdownlist. Huge info-dump is one option; something you can type at theinteractive prompt to provide a different fingerprint format isanother [this is what we did].
- The readonly edit box displaying the fingerprint in Windows (GUI)PuTTYgen. The obvious approach here is to have an option in the menu barthat selects the format [so we did that].
- The GUI key list window in Windows Pageant. That window doesn'thave a menu bar at the moment, but cluttering the window with a set ofradio buttons seems a bit intrusive. Perhaps we should add a menu bar.[We added a drop-down.]
- The fingerprint output mode in Unix (command-line) PuTTYgen.Probably we do this one by making
-O fingerprintand itssynonym-luse the current default fingerprint style, andthen add extra explicit modes like-O fingerprint-md5-hexor-O fingerprint-sha256-base64. [We added-E md5instead.] - The fingerprints in the output of
pageant -lon Unix.A command-line option is the obvious way to select these.[We added--fptype.] - The idiom on Unix Pageant's client command line that lets youselect one of the currently loaded keys by typing a prefix of itsfingerprint. [We added
sha256:andmd5:prefixes.] - The configuration option in PuTTY itself which allows you to enterthe fingerprint of a host key you want PuTTY to accept. We'd have toaccept fingerprints in all formats, and do it in some way that ensuredthey were unambiguous (no fingerprint intended to be type X should beaccepted on the grounds that it matched some key's type-Yfingerprint). [We added a
SHA256:prefix; you canoptionally specifyMD5:too.] - The diagnostic message in PuTTY's Event Log. That's text-only (andalso goes to log files), so once a fingerprint has been written intoit, it's too late to rewrite it in a different style. Perhaps that oneshould just print all available fingerprint types. [We just printSHA-256.]
- Diagnostic messages in Unix Pageant (only relevant in debug mode,so not vital). [Ditto.]
We have been dragging our feet about this, as the new OpenSSH schemehas some disadvantages, principally that it is harder to compare byhand and read out over the phone, as it makes no concession to thepossibility of confusing homographs (letter-l versusnumber-1, O-vs-0 etc).
Ssh Sha256 Md5
We did half-work-out an alternative scheme based on thethe Uniform Data Fingerprint (UDF) scheme described indraft-hallambaker-udf.That scheme has been designed for readability while remaining relativelycompact, to minimise the risk of ambiguity, and to allow easymigration to new hash algorithms (the first character encodes thealgorithm); it would give fingerprints of the formMBQPX-76TZY-NXTKU-WJZIM-LH4T2-IYQU6.Our effort got as far as a half-written spec and some minimalproof-of-concept code, both unpublished. (However, the opportunemoment to push this as a replacement for OpenSSH's scheme hasclearly passed.)
2021-03-14: multiple formats are now supported, and theOpenSSH-style SHA256 fingerprint (SHA-256 of the standard public keyblob, base64-encoded, with trailing = stripped) is nowthe default.
Sftp Sha256
