- 1password Aws Credentials
- 1password 2 Factor
- 1password Aws Iam
- 1password Aws Mfa
- 1password Aws Account Id
- 1password Aws Login
Multi-Factor Authentication or MFA, is a common security precaution used to prevent someone from gaining access to an account even if an attacker has your username and password. With MFA you must also have a device that generates a time based one time password (TOTP) in addition to the standard username/password combination. The extra time it might take to login is well worth the advantages that MFA provides. Having your AWS account hijacked could be a real headache.
- To create a custom password policy (console) Sign in to the AWS Management Console and open the IAM console at. In the navigation pane, choose Account settings. In the Password policy section, choose Change password policy.
- Open and unlock 1Password, select the Login item for the website, then select Edit. Select to the right of the field (Shift + Enter) and choose One-Time Password. Click and choose “From my screen” to scan the QR code. If you can’t scan the QR code, make sure it’s visible when you minimize 1Password.
- AWS Secrets Manager is most compared with HashiCorp Vault, CyberArk Enterprise Password Vault, LastPass Enterprise, 1Password and Thycotic Secret Server, whereas Microsoft Azure Key Vault is most compared with HashiCorp Vault, CyberArk Enterprise Password Vault, Thycotic Secret Server, ManageEngine Password Manager Pro and LastPass Enterprise.
- Password Change Password Policy Requirements (SOA Users Only).WARNING. Only authorized users may access this system. Unauthorized access/tampering is punishable under Alaska Criminal Statutes AS11.46.200, AS11.46.484, AS11.46.740.
Setting it up is pretty easy. First login to your AWS account. I’m security my root user account so I’m going to the IAM console and looking at the dashboard. As you can see I have a very unsightly orange/yellow exclamation mark in my security status dashboard. If you’re like me, we can’t have any of those hanging around. Click the dropdown and then select the “Manage MFA” button.
With 1Password Business, you can automate many common administrative tasks using the 1Password SCIM bridge. It uses the System for Cross-domain Identity Management (SCIM) protocol to connect 1Password with your existing identity provider, like Azure Active Directory, Okta, OneLogin, or Rippling.
A dialogue window will pop up asking what kind of device to use. I’m using my smartphone which isn’t quite as secure as a hardware MFA device, but still pretty good. Click the “Next Step” button.
The next screen is just letting you know that you’ll need to install an AWS MFA compatible application on your phone. I’m using OKTA Verify which works fine, but there are others you can download such as Google Authenticator or Authy. For more information on this see: https://aws.amazon.com/iam/details/mfa/.
Once you’ve installed an MFA app on your phone click the “Next Step” button.
1password Aws Credentials
On the next screen you’ll be given a QR code to scan with your MFA application that was just installed on your device. Scan the QR code that pops up on the screen. After this, you’ll need to put in the next two codes that your MFA app provides so that it sync’s with AWS. When you’re done with this step, click the “Activate Virtual MFA” button.
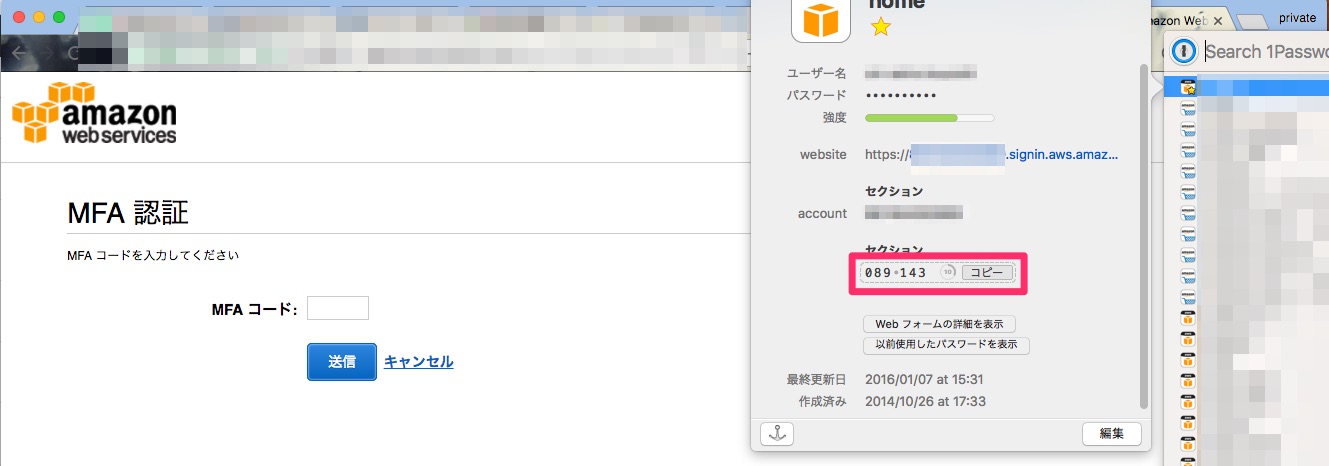
NOTE: You should screenshot the QR code and store it in a SAFE PLACE! If you lose your phone or something or need to reset your MFA, you’ll need to re-scan this QR code. You can’t retrieve this QR code again from the AWS console so it’s up to you to store it in a safe place. I store mine within my 1Password vault along with my AWS credentials.
If all went well you’ll get a success message.
If we look at the IAM dashboard again, we’ll see our green checkmarks and we’re good to go.
“If the light is green, the trap is clean” -Ray Stanz
1password 2 Factor
When we go to login to the AWS account the next time, we’ll be prompted to enter in a one time password after entering the username and password.
Note: You are viewing the documentation for an older major version of the AWS CLI (version 1).
AWS CLI version 2, the latest major version of AWS CLI, is now stable and recommended for general use. To view this page for the AWS CLI version 2, click here. For more information see the AWS CLI version 2 installation instructions and migration guide.
[ aws . ecr ]
Description¶
To log in to an Amazon ECR registry
This command retrieves and displays an authentication token using the GetAuthorizationToken API that you can use to authenticate to an Amazon ECR registry. You can pass the authorization token to the login command of the container client of your preference, such as the Docker CLI. After you have authenticated to an Amazon ECR registry with this command, you can use the client to push and pull images from that registry as long as your IAM principal has access to do so until the token expires. The authorization token is valid for 12 hours.
This command is supported using the latest version of AWS CLI version 2 or in v1.17.10 or later of AWS CLI version 1. For information on updating to the latest AWS CLI version, see Installing the AWS CLI in the AWS Command Line Interface User Guide.
See 'aws help' for descriptions of global parameters.
Synopsis¶
Options¶
1password Aws Iam
None
See 'aws help' for descriptions of global parameters.
Examples¶
To retrieve a password to authenticate to a registry
The following get-login-password displays a password that you can use with a container client of your choice to authenticate to any Amazon ECR registry that your IAM principal has access to.
1password Aws Mfa
Output:
1password Aws Account Id
To use with the Docker CLI, pipe the output of the get-login-password command to the dockerlogin command. When retrieving the password, ensure that you specify the same Region that your Amazon ECR registry exists in.
1password Aws Login
For more information, see Registry Authentication in the Amazon ECR User Guide.
